 illustration from Zenarmor
illustration from Zenarmor
The Future of Cybersecurity: Staying Ahead of Evolving Threats
In an increasingly interconnected world, cybersecurity is paramount. This article explores emerging threats, innovative solutions, and proactive strategies for digital protection.
The Evolving Threat Landscape
Understanding the dynamic threat landscape is crucial for building a robust cybersecurity posture.
Key Threats:
- AI-Powered Attacks: Cybercriminals leverage AI for efficient, hard-to-detect attacks.
- IoT Vulnerabilities: Poorly secured IoT devices are exploited to access networks and steal data.
- Supply Chain Attacks: Targeting software and hardware supply chains for widespread access.
- Ransomware Evolution: Increasingly large ransom demands and double extortion tactics.
- Cloud Security Challenges: Misconfigurations and insider threats in cloud environments.
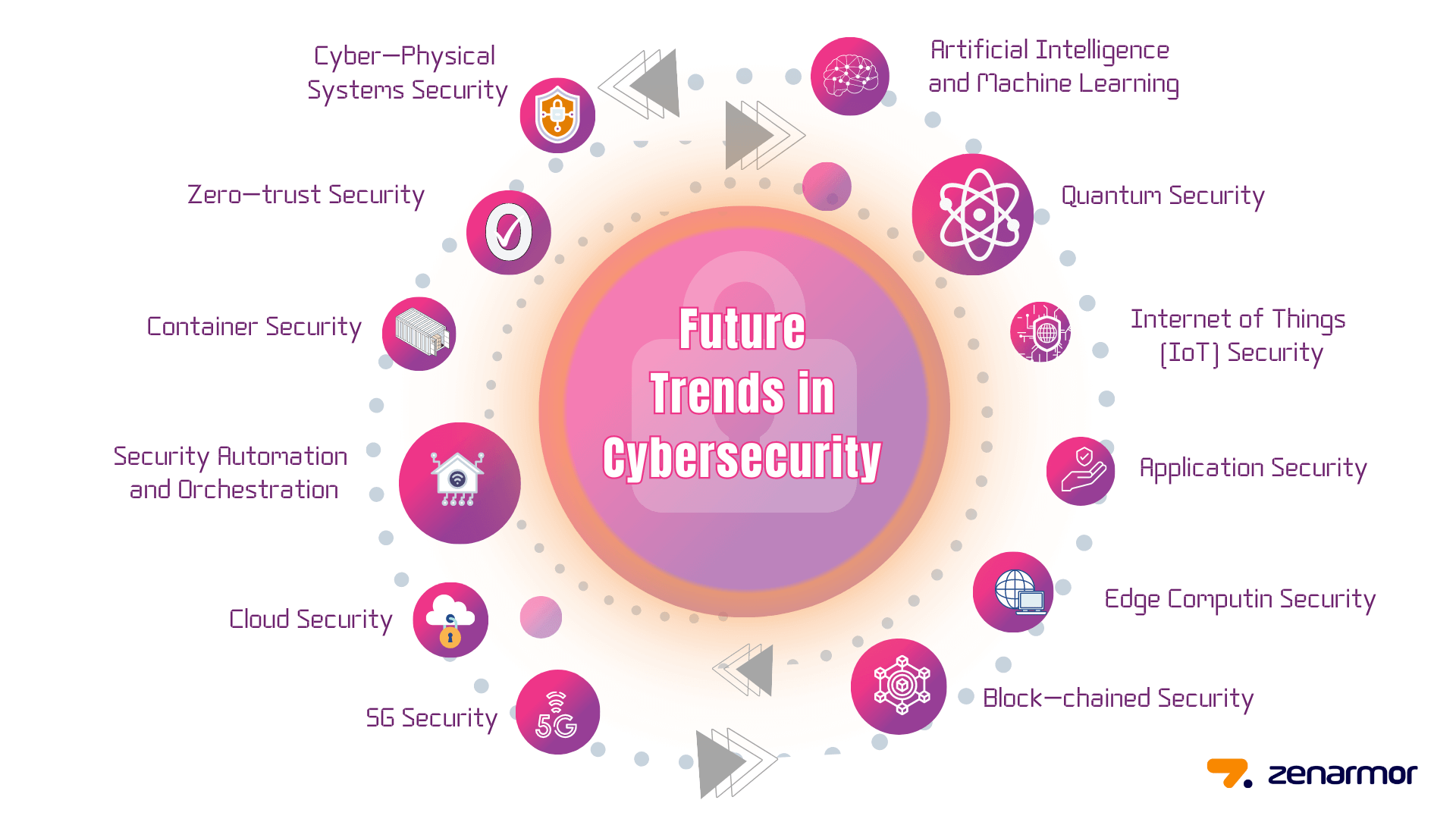
Innovative Solutions for the Future of Cybersecurity
Organizations must adopt cutting-edge technologies to stay ahead of evolving threats.
Key Solutions:
- AI-Driven Cybersecurity: Automating threat detection, incident response, and vulnerability management.
- Zero Trust Architecture: Verifying every access request, regardless of origin.
- Security Automation and Orchestration: Automating repetitive tasks and streamlining incident response.
- Blockchain for Cybersecurity: Enhancing identity management, device authentication, and threat intelligence sharing.
- Quantum-Resistant Cryptography: Protecting against attacks from quantum computers.
Strategies for Staying Ahead of Evolving Threats
Effective cybersecurity strategies are essential for proactive defense.
Key Strategies:
- Proactive Threat Hunting: Actively searching for threats that evade traditional defenses.
- Continuous Vulnerability Management: Regularly scanning for and remediating vulnerabilities.
- Cybersecurity Awareness Training: Educating employees to protect against phishing and malware.
- Incident Response Planning: Outlining steps for identifying, containing, and recovering from security breaches.
- Collaboration and Information Sharing: Sharing threat intelligence to improve collective defenses.
The Role of Government and Policy
Governments play a crucial role in shaping cybersecurity through standards, regulations, and international cooperation.
Key Government Roles:
- Cybersecurity Regulations: Setting standards for data protection and accountability.
- Public-Private Partnerships: Combining expertise and resources to address cybersecurity challenges.
- International Cooperation: Combating cybercrime and establishing common standards.
The Human Element in Cybersecurity
Employees and customers are critical to security. Organizations must invest in awareness training and promote a culture of security.
Key Human Element Strategies:
- Social Engineering Awareness: Helping employees recognize and avoid manipulation tactics.
- Insider Threat Mitigation: Implementing measures to mitigate risks from insiders.
- Promoting a Culture of Security: Making security a shared responsibility through training and communication.
The Future of Cybersecurity: A Proactive Approach
A proactive, adaptive approach is essential for protecting digital assets and staying ahead of evolving threats. Invest in cybersecurity and promote a culture of security.
Call to Action
Strengthen your cybersecurity posture today! Contact us for a free consultation and expert guidance. Visit our website or call us to schedule an appointment.
Published on March 26, 2025
reference: Various cybersecurity news websites and research papers
Gema
Wordsmith and content writer passionate about creating high-quality content that informs, entertains, and inspires. Let me bring your brand's story to life.
All stories by : Gema

0 Comments